| Previous | Table of Contents | Next |
Identifying and Filtering Routes Based on the NLRI
To restrict the routing information that the router learns or advertises, you can filter based on routing updates to or from a particular neighbor. The filter consists of an access list that is applied to updates to or from a neighbor. In figure 10-2, RTD in AS2 is originating network 192.68.10.0/24 and sending it to RTF. RTF will pass the update to RTA via IBGP, which in turn will propagate it to AS1. By doing so, AS3 could become a transit AS advertising reachability of network 192.68.10.0/24.
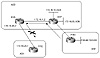
Figure 10-2 Identifying and filtering prefixes.
To prevent this situation from happening, RTA will configure a filter to prevent prefix 192.68.10.0/24 from propagating to AS1. This is demonstrated in the following configuration for RTA:
router bgp 3
no synchronization
neighbor 172.16.1.2 remote-as 3
neighbor 172.16.20.1 remote-as 1
neighbor 172.16.20.1 distribute-list 1 out
no auto-summary
access-list 1 deny 192.68.10.0 0.0.0.255
access-list 1 permit 0.0.0.0 255.255.255.255
In the preceding configuration, the combination of the neighbor distribute-list router configuration command and access-list 1 prevents RTA from propagating prefix 192.68.10.0/24 to AS1. The access list portion of the configuration identifies the prefixes, whereas the distribute list portion applies the filtering on the outgoing updates (note the out keyword). Note that access-list 1 ended with a logic that permits all updates (permit 0.0.0.0 255.255.255.255). When using access lists for filtering, if no action is specified at the end of the access list statements, the logic of "deny everything else" applies. This means that anything that did not match any of the access list instances will be denied. This is why it is important to specify the default action; in this example, 192.68.10.0/24 will be denied, and everything else will be allowed.
Notes:
Route maps could have been used to filter updates in the previous example. The distribute list method was chosen to give you different options for doing filtering.
Using access lists to filter supernets or ranges of updates is a bit trickier. Assume, for example, that RTF in figure 10-2 has different subnets of 172.16.X.X, and you want to advertise an aggregate of the form 172.16.0.0/16 only. The following standard access list would not work because it permits more than is desired. The standard access list looks at the source IP address only and cannot check the length of the network mask. The following access list will permit 172.16.0.0/16, 172.16.0.0/17, 172.16.0.0/18, and so on:
access-list 1 permit 172.16.0.0 0.0.255.255
To restrict the update to 172.16.0.0/16 only, you have to use an extended access list of the form:
access-list access-list-number {deny | permit} protocol source
source-wildcard destination destination-wildcard | mask mask-wildcard
This defines an extended access list that matches on a source destination or a source mask tuple, to permit or deny a specific routing update. The access list number falls between 100 and 199. In the case where the protocol is IP and we are checking on a source/mask tuple, this would translate into:
access-list access-list-number permit ip network-number network-do-not-care-bits mask mask-do-not-care-bits
For example:
access-list 101 permit ip 172.16.0.0 0.0.255.255 255.255.0.0 0.0.0.0
(where a "0" is an exact match bit, and a "1" is a do-not-care-bit).
The preceding extended access list indicates that aggregate 172.16.0.0/16 is to be sent only because we have indicated that the mask should match 255.255.0.0 exactly. An update of the form 172.16.0.0/17 will not be allowed.
Identifying and Filtering Routes Based on the AS_Path
Filtering routes based on AS_path information becomes handy when filtering is needed for all routes of the same or multiple ASs. It is an efficient alternative to listing hundreds of routes one-by-one as may be required to filter on a prefix basis.You can specify an access list on both incoming and outgoing updates based on the value of the AS_path attribute.
Referring still to figure 10-2, if AS3 wanted to prevent itself from becoming a transit AS for other ASs, AS3 can configure its border routers RTA and RTF to advertise only local networks. Local networks originated from the AS itself. This can be done with the following RTA configuration; RTF will be configured in the same manner.
RTA configuration:
router bgp 3
no synchronization
neighbor 172.16.1.2 remote-as 3
neighbor 172.16.20.1 remote-as 1
neighbor 172.16.20.1 filter-list 1 out
no auto-summary
ip as-path access-list 1 permit ^$
In the preceding RTA configuration, the as-path access list 1 identifies only updates that originate from AS3. The filter list works in conjunction with the as-path access list to filter the updates. In this example, the filter list is applied on the outgoing updates (note the out keyword). The regular expression ^$ indicates an AS_path that is empty. The "^" symbol indicates the beginning of the AS_path, and the "$" symbol indicates the end of the AS_path. Because all networks originating from AS3 have an empty AS_path list, they will be advertised. All other prefixes will be denied.
If you want to verify that your regular expression works as intended, use the following EXEC command:
show ip bgp regexp regular-expression
The router displays all the paths that match the specified regular expression.
Notes:
Route maps could have been used to filter updates in the previous example. The filter list was chosen to give you a different option for filtering.
| Previous | Table of Contents | Next |