| Previous | Table of Contents | Next |
Policy Routing
Policy routing is a means of controlling routes that relies on the source, or source and destination, of traffic rather than destination alone. Policy routing can be used to control traffic inside an AS as well as between ASs. Policy routing is a glorified form of static routing. It is used when you want to force a routing behavior different from what the dynamic routing protocols dictate.
Troubleshooting: Ch. 11, pp. 418-422. Policy Routing
Static routing enables you to direct traffic based on the traffic destination. Traffic toward destination 1 can go via point A whereas traffic toward destination 2 can go via point B.
Policy routing, on the other hand, enables you to direct traffic based on traffic source or a combination of source and destination. Traffic coming from network 1 can go via point A, or traffic coming from network 1 and going toward network 2 can go via point B.
Consider the example illustrated in figure 7-6. Assume that AS1 was assigned network numbers from two different providers. The 10.10.10.0/24 range was taken from AS3, and the 11.11.11.0/24 range was taken from AS4. AS1 wants to have any traffic originated from its 10.10.10.0/24 networks to be directed toward AS3 and traffic from its 11.11.11.0/24 networks to be directed to AS4, irrespective of the destination of the traffic. AS1 could use policy routing to achieve this requirement by forcing all traffic with a source IP address belonging to 10.10.10.0/24 to have a next hop of 1.1.1.1, and traffic with source IP belonging to 11.11.11.0/24 to have a next hop of 2.2.2.2.
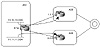
Figure 7-6 Policy routing scenario based on source.
Policy routing can also be based on a source/destination combination. This is illustrated in figure figure 7-7. Assume that RTA wants to use the SF link for any traffic originating from network 10.10.10.0/24 and reaching network 12.12.12.0/24 in NY. Also, RTA wants to use the SJ link for any traffic originating from network 10.10.10.0/24 and reaching network 13.13.13.0/24 in NY. Policy routing can be used to set the next hop for the traffic combination (Source = 10.10.10.0/24, Destination = 12.12.12.0/24) to be 1.1.1.1. The traffic combination (Source = 10.10.10.0/24, Destination = 13.13.13.0/24) will be set with next hop 2.2.2.2.
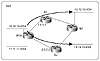
Figure 7-7 Policy routing scenario based on source and destination.
Whenever static behavior is enforced, backup becomes an issue. It is important to make sure that if policy routed traffic cannot be delivered because the next hop is down, some other alternative is available. Cisco offers a creative way of doing policy routing by offering multiple next hops for policy routed traffic. If the first next hop is down or not available, the second next hop will be tried, and so on. If none of the statically defined next hops are available, the router can be configured to send the traffic according to the normal dynamic routing (that is, based on destination). This is illustrated in figure 7-8.
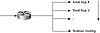
Figure 7-8 Policy routing defaults to dynamic routing.
Other Applications of Policy Routing
One practical application of policy routing is its use with firewalls. Firewalls are devices that apply security requirements to traffic. Firewall implementations include packet filtering, authentication, and encryption. Depending on the network setup, administrators might want to direct some or all incoming (or outgoing) traffic toward a firewall device (see figure 7-9).
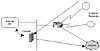
Figure 7-9 Incoming or outgoing traffic can be routed to a firewall.
An applicable situation might involve traffic entering an organization through dialup services. Perhaps the organization requires that the dialup users from remote sites pass through a firewall before reaching the Internet. If the firewall is in the traffic trajectory, this is not a problem. Any inbound or outbound traffic will pass through the firewall on its way to a destination. In some cases, however, (such as that shown in figure 7-9), traffic bypasses the firewall in its normal path. Policy routing can be configured on a router bordering external networks, to force the incoming traffic to be directed to the firewall. After the firewall applies its policies or encryption, traffic will be sent to its destination.
Notes: Policy routing does not change the traffic destination. It affects only the next hop to which traffic is directed prior to being sent along toward its destination.
Policy routing can also be used with dialup services for better traffic balancing, as illustrated in figure 7-10. Dialup users accessing a certain point of presence can be directed toward certain providers based on their source IP address. As illustrated in figure 7-10, dialup users in region 1 can be directed toward provider 1, whereas dialup users from region 2 can be directed toward provider 2.
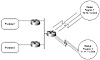
Figure 7-10 Balancing dialup traffic based on source.
Policy routing should not replace dynamic routing, but instead should complement it. Policy routing has its own set of drawbacks.
- 1. Extra configuration is needed to identify sources of traffic or a combination of source and destination. Care should be taken not to disrupt other traffic and to specify other alternatives for traffic in case of backup situations.
- 2. Policy routing is CPU-intensive because it is based on the source IP addresses, unlike dynamic and static routing, which are based on the destination IP addresses. Sophisticated caching and switching techniques have been implemented all along based on the destination of the traffic. Most implementations have not yet optimized routing and caching techniques based on the source of the IP packet. As such, policy routing takes additional CPU cycles to detect source addresses. This behavior should change as implementations move toward better understanding of IP traffic flows that enable caches to keep track of source and destination information. This new caching methodology would alleviate routers from disruptive processing on matching sources of IP traffic and make policy routing much more effective and practical.
| Previous | Table of Contents | Next |